From Missiles to Microchips: The Strategic Tech Terrain in Israel’s War
In this special edition of Technopolitik, the Takshashila team provides insights into some technological aspects of the ongoing war in West Asia.
If you like the newsletter, you will love to read our in-depth research and analysis at https://takshashila.org.in/high-tech-geopolitics.
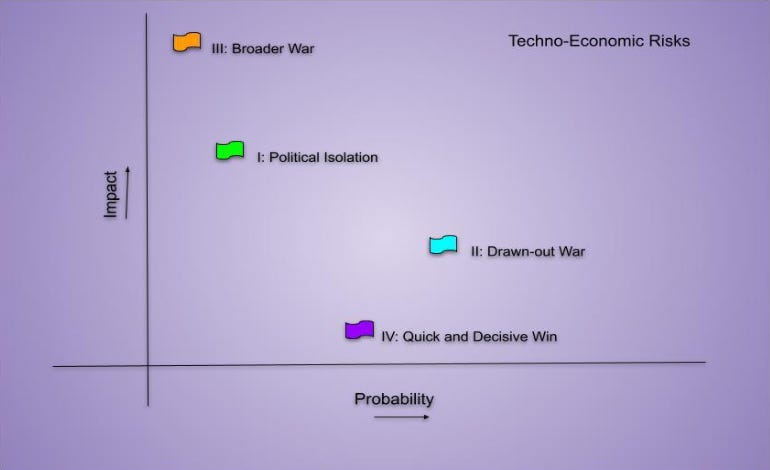
In November 2023, the Takshashila team wrote a working paper attempting to predict the techno-economic impact of the (then) Israel-Hamas war on India’s interests. In the paper, we decided to adopt a scenario-based analysis to analyse the possible repercussions of the conflict. The four scenarios we posited were:
I) Israel is politically discredited in the aftermath of the war. Partner countries, except the USA, distance themselves politically and economically to avoid getting tainted.
II) Israel enters a drawn-out war with Hamas, resulting in widespread internal instability, prolonged strife and terrorism across its entire territory.
III) The Israel-Hamas war spills over its borders, and a broader war is ignited, with multiple regional and international powers getting involved.
IV) Israel wins decisively, ending the conflict quickly. The war ends with the installation of a pliable govt in Gaza.
Figure 1: Authors’ Visualisation
You can read the paper here for a detailed breakdown of India’s interests and our brief analysis. However, it is clear now that Israel’s response to the October 7, 2023 attacks has escalated to involve neighbouring states and other actors beyond Hamas. As of now, we can broadly suggest that this is both a broader and a drawn-out war, albeit Hamas’s role may no longer be the sole adversary for Israel, with an all-out war with Iran and its “axis of resistance” seemingly imminent.
In this edition, Aditya Ramanathan and Satya Sahu comment on how the conflict has affected some facets of Ballistic missile defence and the global semiconductor supply chain. Col. KPM Das then discusses and analyses the implications of the pager and walkie-talkie supply chain attacks that Israel carried out against Hezbollah and other Lebanese individuals.
On Ballistic Missile Defence
—Aditya Ramanathan
There is much that is unprecedented about Israel’s now year-long war in West Asia. Among these unprecedented actions are the two direct missile and drone volleys Iran has launched in retaliation for Israeli actions.
The attacks have difficult lessons for India. These difficulties arise not just because of the potential of drones or because of the democratisation of precision guidance but also because conventional ballistic missiles are a reality India cannot ignore.
While drones and cruise missiles create significant new challenges, they can be blunted to some degree by modifying and bolstering existing air defences, including air-to-air missiles, surface-to-air missiles (SAMs), and close-in weapon systems (CIWS).
On the other hand, defending against ballistic missiles presents a much harder technological challenge. This is underscored by the American decision to station a Terminal High-Altitude Area Defense (THAAD) battery in Israel. Beyond the technological hurdles and costs, ballistic missile defence (BMD) is integral to nuclear strategy, creating new strategic complications.
What Iran Did
Iran mounted the first of its two attacks on the night of 13/14 April. The volley apparently involved 185 propeller-driven drones, 36 jet-powered drones or cruise missiles (the distinction is arbitrary), and 110 ballistic missiles. Israel’s multilayered air defence intercepted many of these. Other missiles or drones were destroyed en route by a US-led coalition that included Jordan, the UK and France. American and Jordanian forces alone reportedly shot down scores of drones from the ground and the air.
According to one assessment, the Iranians employed three types of ballistic missiles. Two of these were rather clunky systems of well-known provenance. One was the Ghader, an upgrade of the better-known Shahab-3. These missiles are not terribly accurate, and their main purpose appears to be to help overwhelm enemy missile defences (and perhaps score a lucky hit). The second type of missile was the Imad, an accurised variant of the Ghader that can perform some amount of course correction in its terminal phase. Israel likely intercepted at least one such missile in an exoatmospheric kill. The third and most accurate type of missile was the Kheibar Shekan, an accurised version of the Fatah 110. This is a missile Iran can plausibly employ to attack point targets.
Part of the reason the April attack was easily blunted was that Iran itself sought to control escalation by clearly indicating its intent and employing several less effective systems. The attack on 1/2 October may have been more effective (though almost equally non-lethal) both because Iran enjoyed a greater element of surprise and because it used ballistic missiles exclusively.
Those missiles included what Iran claimed was a “hypersonic” variant of its Fatah missile. As with so much else about hypersonic weapons, this claim is likely just hype. As Fabian Hinz argued last year, the missile does not seem to possess a hypersonic glide vehicle (HGV), which can manoeuvre in the Earth’s atmosphere to evade missile defences. Instead, it is probably a standard medium range ballistic missile (MRBM) with some amount of manoeuvrability for greater accuracy. What makes the missile more potent is not some exotic hypersonic capability but its use of solid propellants and its greater capacity for precision. We should also note that MRBMs and other longer-range ballistic missiles reach hypersonic speeds in their terminal phases anyway.
The Difficulty of BMD
Effective BMD remains one of the most daunting challenges in missile applications, often likened to trying to “hit a bullet with a bullet”. The United States maintains a significant lead in BMD over the rest of the world, with its Ground-based Midcourse Defense (GMD), and its ship-based Aegis systems with the SM-3 series of missile interceptors. These midcourse defences are supplemented by the THAAD system.
Despite the sophistication of these defences, they stand little chance against significant nuclear arsenals. Even the GMD, which is perhaps the most advanced space weapon ever created, has, at best, a 55% chance of successfully intercepting an ICBM. Given that these extremely expensive interceptors are also fielded in small quantities, they would be quickly overwhelmed during a full-scale nuclear exchange.
However, BMD systems are more effective against MRBMs and Intermediate Range Ballistic Missiles (IRBMs). This begins to matter when dealing with volleys of conventional missiles. Unfortunately for defenders, these interceptors offer a terrible exchange ratio, being far more expensive than the missiles they stop. For instance, the Block II-A variant of the SM-3, costs about $36 million each.
India’s Dilemma
India has a modest BMD programme of its own focused on intercepting missiles in the 2000-5000 km range. Like other governments, India justifies the existence of this limited arsenal by saying its BMD is primarily meant to intercept stray missiles from rogue or accidental launches and not meant to engage in nuclear warfighting. While this is undoubtedly true, there are other reasons to pursue such a programme. One, BMD serves as a useful technological hedge in the event that major new advances are made in missile interception. Two, BMD systems make for effective direct ascent antisatellite (DA-ASAT) weapons, at least in low Earth orbit (LEO).
However, if there’s a BMD lesson for India from the ongoing war, it’s that conventional ballistic missiles are a serious threat. For instance, in the event of a ground war along the Line of Actual Control (LAC), China would have strong incentives to attack Indian air bases and lines of communication, directly aiding the war effort. Such attacks may employ multiple vectors, including fixed-wing aircraft and cruise missiles, as well as MRBMs or IRBMs that are far more sophisticated than the ones Iran presently fields.
To dissuade ballistic missile attacks, India has two options that are not mutually exclusive. One is to bolster India’s BMD, a move that may be necessary but will prove expensive and likely fuel a further expansion of Pakistan’s nuclear arsenal. The other is to develop a new family of exclusively conventional ballistic missiles that can deter by punishment. To channel Stanley Baldwin, some ballistic missiles will always get through. All India may be able to do is to ensure its adversary pays a price.
The Semiconductor Supply Chain
— Satya Sahu
Beyond East Asia, Israel is one of the few places in the world where advanced chips are designed and produced and is a major hub for top semiconductor companies’ R&D centres alongside a bustling homegrown startup scene. While investment levels in the country’s high-tech sector have remained more or less the same, the risk appetite for semiconductor companies may lessen as the conflict expands and continues. Both Israel’s mobilisation of IDF reservist brigades over the course of this conflict (which has affected the supply of talent to these technology companies), and the escalation of this conflict have affected their normal operations and output.
The primary casualty of the broadening war is arguably Intel. Intel has suspended the construction and development of its Fab 38 facility in Kiryat Gat despite having committed to an investment of almost $ 25 billion by the end of 2023. IDF mobilisation and a constant threat of bombardment could also feasibly have impacted the operation of its existing Fab 28 facility. In the aftermath of October 7, the IDF’s blockade on Gaza significantly affected its operations as well, since Palestinians crossing over to Israel for work were instrumental in areas like transport and logistics, etc. It is unclear as to whether Intel has been able to manage this shortfall in personnel.
The suspension amidst a troubled restructuring has almost definitely factored into Intel’s recent decision to split its product and foundry (Intel Foundry Services) divisions off as separate entities. The costs of running fabrication foundries at the leading-edge are highly prohibitive, running up to anywhere from $10 to $20 billion. The fact that the US’ only option for fabricating advanced chips finer than 7nm has run into such dire straits does not bode well for President Biden’s policy goals for achieving greater semiconductor supply chain resiliency. Amidst setbacks to its expansion plans, such as Fab 38’s suspension, slumping revenue, and massive layoffs, Intel’s promised $8.5 billion in CHIPS Act subsidies have been slow to come through, as US officials attempt to vet the viability of its roadmap.
Either way, Intel is far too critical to the US’ ambitions to shore up domestic capabilities in chip manufacturing and will likely receive more support. However, if the current conflict results in further and exacerbated disruptions in the activities of its Israeli facilities, Intel’s projected roadmap will be in a lot of trouble, as replacing fabrication capacity would take at least 3-4 years.
Besides this, uncertainty surrounding the availability of critical production inputs and finished chips can continue to rise as the conflict expands; shipping traffic levels through the Suez Canal have gone down in the aftermath of the October 7 attacks, and higher incidence of Houthi attacks on commercial vessels. If Israel enters into an all-out war with Iran, this shipping lane will invariably be affected, resulting in significantly higher costs of components and disruptions in the availability of critical chips to downstream industries.
However, as Col. KPM Das explains in the next section, the greatest concern to nation-states would now be the demonstrated feasibility of orchestrating large-scale supply chain attacks that take advantage of the complex and fragmented nature of the world’s high-tech hardware. Beyond the prospect of compromised consumer electronics hardware being used for indiscriminate or targeted attacks, there is now a not-so-remote possibility that hard-to-detect chip-based hardware backdoors may be present in critical computing hardware. This makes things more complicated for policymakers seeking to ensure the trustworthiness and security of computing hardware in the absence of any robust supply chain audit mechanisms.
Lessons from Lebanon
-Col. KPM Das
Background
On the 17th and 18th September, pagers in the hands of many people in Lebanon exploded, causing injuries and deaths on a large scale. Most of the devices were used by members of Hezbollah. Pagers certainly have a lower electronic envelope than cell phones, which must have been the motivation to use in command-and-control communications. Unlike cell phones, whose design and hardware enable two-way voice, data and video communications, pagers are simple devices with one-way text communications with associated source identifiers. Later, walkie-talkies exploded at the funerals of victims killed earlier. What followed was mayhem, with reports of other electronic products also targeted. The pagers and walkie-talkies were traced to Original Equipment Manufacturers (OEMs) from Taiwan and Japan, respectively, with the principal channel supplier in Hungary. All of them denied responsibility.
Clearly, both pagers and walkie-talkies are low-end electronic devices with the possibility of counterfeit sources, and hence, supplier attribution remains a challenge. It also appears the vintage manufacturing of the pagers make AR-924 and walkie-talkies make ICOM is unknown.
There were definite accounts from victims that the pagers were supplied five to six months ago. The pager network appears to be the first line of communication among Hezbollah members since then. There are also reports of a Lebanese security official indicating that about 5,000 pagers were received in one lot.
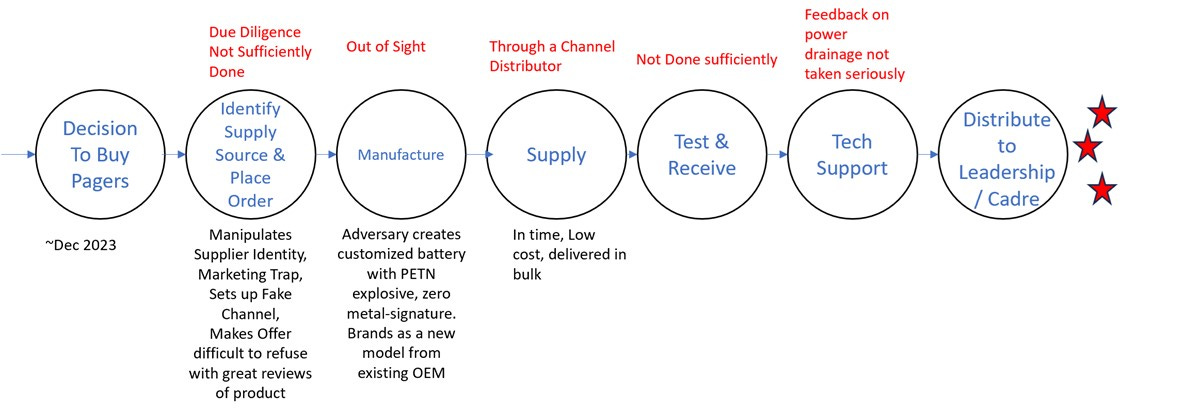
An assessment of the attack vectors reveals that the hardware supply chain was compromised at multiple points in the supply chain and was taken over by Israel Defence Forces (IDF) at various points in the past. Malicious components and specific low signature, pre-implanted explosives were inserted and activated via a radio signal, maybe the paging signal itself. From the reports, it appears this was not a single point of compromise in the chain. It seems quite likely that right from the time a procurement enquiry was initiated by Hezbollah leadership, their adversaries “captured” the supply chain cycle, including the receiving of supply orders, the securing of the devices, re-engineering of the hardware at scale, comprehensive testing and then reinjection into the supply chain. Necessarily, this exercise was controlled right from sourcing to the supply through a final and innocuous front-end distributor in Europe.
A multi-stage supply chain scenario of the pagers and walkie-talkies used by Hezbollah would look possibly like this with a likely set of actions and process failures marked. This has been described in the Reuters report by Mark Gebeily, James Pearson and David Gauthier-Villars
Figure 2. Author’s Visualisation
We can see that interdiction and manipulation of parts and components is physically possible at any stage in this cycle. While it is easier in software-based attacks to fix issues by resets to manufacturer defaults, it is difficult in hardware attacks since the persistence of malicious actions is severe.
Another example of a hardware supply chain attack is from 2016, when Baseboard Management Controller (BMC) vulnerabilities were injected across Lenovo, Intel and Super Micro server boards and were later widely reported. BMCs, (micro-computer chips on motherboards), provided administrators the ability to system-manage servers remotely in a “lights out” configuration. The randomisation of address layouts is a critical feature that helps combat hacks, and that feature was removed by exposure to this vulnerability. These firmware vulnerabilities were attributed to an open-source component lighttpd, and were not fixed for years. This is a classic example that demonstrates the tight coupling that happens between hardware and software in the supply chain.
Factor: Interdiction of the Supply Chain
As with the pagers which exploded in the hands of the Hezbollah members, interdiction of the hardware supply chain by malicious actors is a potential risk. While it is not as easy as poisoning or tampering with software in the supply chain, the hardware supply chain remains a risk. Given the length of the supply chain, we could have any of the stages being compromised by an attacker. This could either take the form of replacing components with programmed and compromised hardware or by modifying the firmware, thus enabling the attacker to set up backdoors, which get activated through many command and control interventions by an adversarial actor. What follows could be control of the hardware and the system by the adversarial actor and potential data exfiltration at scale.
Given that the supply chain is global, with manufacturing sites spread across geographies, “seeding” the hardware with malicious components or insertion of explosive circuitry will require physical intervention in the site or capture of an entire supplier ecosystem (as in the case of the pager attacks). It takes a determined attacker, often at a state actor level, to carry off a successful seeding attack of this kind.
Factor: Complexity of the Hardware Supply Chain
A maze of companies come together to finally place a product in the hands of the customer. Contrary to common belief, it is often not one manufacturing site where the products get made. Instead, after the product design is done by the OEM company, the downstream supply chain takes effect, and multiple levels of outsourcing occurs, involving many vendors.
Further, components are supplied by another set of component suppliers who are contracted through Master Supplier Agreements. Often, after manufacturing in a factory, the PCBs (printed circuit boards and other accessories) are shipped to an assembly vendor who finally ships the completed product. At this stage, firmware gets loaded and tested. In summary, we have a complex series of companies that come together to make a product; many would not even know other entities in the same process. The lack of traceability, low transparency and multiplicity of players in the manufacturing and supply process makes the hardware supply chain so complex.
Factor: Securing the Supply Chain Carries Significant Effort and Cost
Supply chains have turned global, with OEMs locating their supplier and manufacturing bases to optimise costs- of components and material, available talent, manufacturing, and final assembly and testing- so that the markets are best served out of sites in proximity. This optimisation objective results in multiple geographies where manufacture, component-sourcing and supply take place, each with associated local market access statutes and exposure to geopolitical dynamics. Past uncertainties and disruptions caused by the pandemic and more recent conflicts in Eastern Europe and West Asia have driven up costs of supply chain security, eventually impacting the costs of electronic products and systems.
What is the Way Ahead?
In retrospect and looking at the September 17th and 18th attacks, here are a few stages which appear to have been points of failure in the Hezbollah hardware supply chain compromise.
A Verified-Inventory List of Suppliers. Given the background of earlier sporadic instances of compromise in the cell phones, Hezbollah made a choice to move to a more passive mode of communication through pagers. It appears that this change was made at short notice, and due diligence took a back seat. Suppliers were not vetted across the supply ecosystem. The veracity of the manufacturer, supply channel and distributor may not have been done at all.
Focus on Critical Points in the Supply Chain. In the Electronic Asset Inventory, Mark and Identify those devices which provide/participate-in critical business services. The O Group, which is the Hezbollah’s command and control network, transitioned to the Pagers with no alternate fallback. In command-and-control networks, there is often a primary mode (pagers in this case) and a secondary fallback mode (radios/cell-phones could have been set up for this mode).
Risk Management Processes. It appears no verification was done- neither of the manufacturer nor of the distribution channels. ICOM in Japan insists the radios were not from their product list, and earlier, Gold Apollo in Taiwan had declined such a pager supply to have been done. Instead, the OEM, Gold Apollo, claims that their channel distributor, BAC Consulting in Hungary, licensed to make and supply had executed the supply order. Reports show that BAC Consulting was only a trading intermediary with no manufacturing experience. In summary, at various stages of the chain (product shortlist, supplier shortlist, sample testing and verification, acceptance testing, third-party validation of supplier etc), risk evaluation and due diligence processes were not in place.
As an organisation procuring hardware, minimal safeguards must be incorporated into the procurement process to reduce risks of exposure to compromised supplies. First, organisations must be sure to pick their supplier from a shortlist of vendors with a verified market reputation and from a verified distributor/channel. Second, in the vetting process, organisations should ask for the supply chain traceability and understand where the assemblies and components come from. Finally, they should ensure that they are informed about the system integrators and the manufacturing partners. If there are options for supply sites, the ones that have more security assurances should be selected.
In organisations with mature security assurance policies and procedures, the procurement office is expected to vet each node in the supply chain for its manufacturing and shipping processes. The NIST Cybersecurity- Supply Chain Risk Management (C-SCRM) recommendations help in prioritising assurance and place a premium on identifying “components that are highly vulnerable and has concomitant highest impact.” Time/Effort/Cost/ Resources must then be mapped to address the highlighted risks. Often, organisations carry out limited onsite supply chain inspections with discretion and this need is baked into the Master Services/Supply Agreements.
However, these recommendations are cost-effective only when the supply volume is large, and products are complex. As we saw in the Hezbollah Pagers supply order, the numbers were in a few thousand and products were commodity-class (low complexity, simple hardware). A process as onerous as this one may not be operationally optimal. However, it is still baffling that for a primary leadership communication network, Hezbollah did not verify the manufacturer nor the channels of supply, which, apparently, had been completely taken over by the IDF.
Conclusion
As a turning point in the conflict, the pager attacks are seen as significant for two reasons: one, a new conflict vector with the potential to disrupt the adversary’s command and control networks has emerged complementary to a kinetic conflict, and two, this event has drawn attention to an area of high technology geopolitics that remained in the realm of a threat but never manifested at large scale until this manifested in Lebanon. We can expect militaries worldwide to look at supply chain security with greater attention and concern. Also, supply chains will certainly be validated and vetted against the geopolitical backdrop to secure a degree of assurance that only trusted supply chain partners from trusted countries can provide.